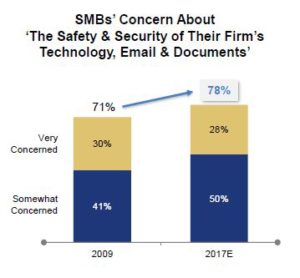
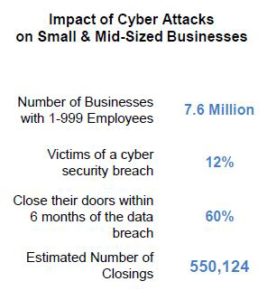
As we reach the annual World Backup Day of the year, it is important to focus on the importance of backing up to avoid losing important files that could have been saved with a simple back-up procedure.
I, for one totally know how this feels following my recent incident of dropping my phone down the toilet, to which the phone became instantly inactive losing over 2000 pictures, files, A LOT! All of which could have been saved if I had just backed up to cloud, but yes I’ve learnt the hard way.
So now here’s the question- shouldn’t back-up day be every day? Does a day dedicated to it really express its true importance and effects?
Well, CBR put together a list with what some experts in this field have to say to answer this mystery.
GDPR
In aid of raising awareness of the risks of losing data and what can be done to prevent it, Cloud computing company, Rackspace shares its views on the importance of UK businesses backing up their data.
Lillian Pang, Senior Director of Legal and Data Protection Officer, Rackspace said: “Every day data becomes more valuable to businesses, with more and more created at an ever-increasing speed. While the message to ‘back up’ data is beginning to resonate, this in turn means that businesses are up to their necks in large amounts of data that needs protecting. And this is just the data they know about, without even thinking of what is going on in shadow IT.
 “Initiatives like World Backup Day serve as a timely reminder to businesses not only of the need to back up data, but also to protect and carefully manage this invaluable asset. Like all risk based strategies, businesses must know what really needs to be backed up in the first place. In other words, businesses must understand what the ‘mission critical data’ actually is.
“Initiatives like World Backup Day serve as a timely reminder to businesses not only of the need to back up data, but also to protect and carefully manage this invaluable asset. Like all risk based strategies, businesses must know what really needs to be backed up in the first place. In other words, businesses must understand what the ‘mission critical data’ actually is.
“The sheer scale of data in circulation means that a simple backup tool is no longer enough in minimising the risk of valuable file or database goes missing or becoming corrupted. In addition, the process of backing up data has become more complex than it used to be because companies are more conscious than ever of the compliance regulations they have to adhere to.
“ If processes aren’t in place to meet legislation like GDPR, it’s not just reputational damage that organisations need to worry about – high fines could also have a significant business impact. Businesses need to dedicate time and resource to implement and execute on the processes in place for identifying and responding quickly to system degradations or failures.”
Disaster Recovery
In response to the importance of regular backups, Cloud service provider, iland shares the idea that backing up data is an easy and hassle-less procedure that can be done daily or any day of the week. Still yet, many organisations and individuals ignore the process for different reasons.
 Brian Ussher, President and Co-Founder, iland said: “On World Backup Day, it’s a good time to recognise how far the market has come in protecting mission-critical business data. The scalability, flexibility and on-demand nature of the cloud means that backup and DR strategies that were previously only available to large enterprise customers are now also within the reach of small and medium sized businesses.
Brian Ussher, President and Co-Founder, iland said: “On World Backup Day, it’s a good time to recognise how far the market has come in protecting mission-critical business data. The scalability, flexibility and on-demand nature of the cloud means that backup and DR strategies that were previously only available to large enterprise customers are now also within the reach of small and medium sized businesses.
“Indeed, many of our customers have evolved from onsite backup to cloud backup to a full cloud-based disaster recovery strategy. While risks ranging from the dramatic; hurricanes, storms and ransomware attacks to the mundane; power outages, unauthorised changes and human error are only increasing, companies of all sizes can be confident that the technology and expert assistance is available to help them achieve IT resiliency and business continuity.”
What do Veeam and Hitachi Data Systems have to say?
Data Centre Action
Again, in response to World Back up Day itself, many look at the risks of making organisations back up on the same day. Not only could it cause a crash in backup locations, but who can be so sure that the process of large amounts of data transfer at once will not cause users files to end up in different locations.
This is why files should consistently be stored in secure locations.
 Jon Leppard, Director, Future Facilities said: “A comprehensive backup policy should involve keeping copies of data on a local server or hard drive, but most importantly it should also be stored in an external location –usually a datacentre. But even datacentres have capacity limits on the volume of data they can store at any one time. If everyone were to back up at the same time there would be considerable pressure on network bandwidth and global data centre capacity.
Jon Leppard, Director, Future Facilities said: “A comprehensive backup policy should involve keeping copies of data on a local server or hard drive, but most importantly it should also be stored in an external location –usually a datacentre. But even datacentres have capacity limits on the volume of data they can store at any one time. If everyone were to back up at the same time there would be considerable pressure on network bandwidth and global data centre capacity.
“Data centre operators must ensure they have a backup strategy in place, in terms of predicting the impact of a sudden spike in demand. After all, backup must be failsafe, or it is of little value. With that in mind, maybe encouraging everyone to backup on one day of the year is not the right approach.”
Availability Gap
As we have a specific day set aside to encourage backing up, it should be just as important to demand continuous availability, especially as businesses are now required to adjust to become the Always-On enterprise to allow 24/7 availability.
For this reason, it is advised that World Availability Day should be imposed the day before World Backup day and should also be given more awareness, according to Veeam.
 Richard Agnew, VP NW EMEA, Veeam said: “In today’s connected world, businesses need to ensure availability to avoid a breakdown in operations.
Richard Agnew, VP NW EMEA, Veeam said: “In today’s connected world, businesses need to ensure availability to avoid a breakdown in operations.
“The recent AWS outage (which took down many large websites for several hours) paints a clear picture that businesses cannot afford to have unavailable data. Not only does brand reputation take a toll, businesses are also left out of pocket. Organisations have become more aware of the dreaded ‘availability gap’ emerging – which includes data loss, extended recovery times, unreliable data protection, and a lack of knowledge of the IT environment leading to unplanned issues and downtime.
“Organisations have implemented innovative solutions and planning which needs to be complemented with processes that can ensure availability at all times. With AI, machine learning and the Internet of Things driving IT modernisation, it’s imperative that data and functionality is protected at all times, and that’s why having a secure website is important, but you can achieve this with the right hosting, and if you don’t know how to host a websites there are guides such as the Introduction to Web Hosting site you can find online and is perfect for this purpose.
“The boardroom discussions need to evolve from the backup and recovery strategy to availability. It’s high time for businesses to take action and introduce an IT strategy that ensures their business is Always-On 24/7.”
Data Storage
For businesses especially, secure enterprise data storage should be of key importance especially considering the upcoming GDPR effects which are due to take place.
Steve Lewis, CTO UK&I, Hitachi Data Systems said: “With just a year to go before organisations operating in the EU must become GDPR-compliant, it’s now more important than ever for companies to focus on safely and securely storing organisational and customer data.
 “The amount of data captured by businesses every day can be a huge asset, unlocking valuable insights and creating competitive advantage. However, this same information can also cause serious headaches for those tasked with securely storing and managing it – and GDPR is putting a time limit on the need to get this right.
“The amount of data captured by businesses every day can be a huge asset, unlocking valuable insights and creating competitive advantage. However, this same information can also cause serious headaches for those tasked with securely storing and managing it – and GDPR is putting a time limit on the need to get this right.
“As a result, it’s no surprise that many organisations are looking to new solutions to help them navigate the regulatory landscape – with Data Protection Officers increasingly being hired to guide organisations and provide a bridge between the IT department and the boardroom, and companies looking for technology solutions to help them better manage and govern the data they hold.”


 +(214) 550-0550
+(214) 550-0550



 “Initiatives like World Backup Day serve as a timely reminder to businesses not only of the need to back up data, but also to protect and carefully manage this invaluable asset. Like all risk based strategies, businesses must know what really needs to be backed up in the first place. In other words, businesses must understand what the ‘mission critical data’ actually is.
“Initiatives like World Backup Day serve as a timely reminder to businesses not only of the need to back up data, but also to protect and carefully manage this invaluable asset. Like all risk based strategies, businesses must know what really needs to be backed up in the first place. In other words, businesses must understand what the ‘mission critical data’ actually is. Brian Ussher, President and Co-Founder, iland said: “On World Backup Day, it’s a good time to recognise how far the market has come in protecting mission-critical business data. The scalability, flexibility and on-demand nature of the cloud means that backup and DR strategies that were previously only available to large enterprise customers are now also within the reach of small and medium sized businesses.
Brian Ussher, President and Co-Founder, iland said: “On World Backup Day, it’s a good time to recognise how far the market has come in protecting mission-critical business data. The scalability, flexibility and on-demand nature of the cloud means that backup and DR strategies that were previously only available to large enterprise customers are now also within the reach of small and medium sized businesses. Jon Leppard, Director, Future Facilities said: “A comprehensive backup policy should involve keeping copies of data on a local server or hard drive, but most importantly it should also be stored in an external location –usually a datacentre. But even datacentres have capacity limits on the volume of data they can store at any one time. If everyone were to back up at the same time there would be considerable pressure on network bandwidth and global data centre capacity.
Jon Leppard, Director, Future Facilities said: “A comprehensive backup policy should involve keeping copies of data on a local server or hard drive, but most importantly it should also be stored in an external location –usually a datacentre. But even datacentres have capacity limits on the volume of data they can store at any one time. If everyone were to back up at the same time there would be considerable pressure on network bandwidth and global data centre capacity. Richard Agnew, VP NW EMEA, Veeam said: “In today’s connected world, businesses need to ensure availability to avoid a breakdown in operations.
Richard Agnew, VP NW EMEA, Veeam said: “In today’s connected world, businesses need to ensure availability to avoid a breakdown in operations. “The amount of data captured by businesses every day can be a huge asset, unlocking valuable insights and creating competitive advantage. However, this same information can also cause serious headaches for those tasked with securely storing and managing it – and GDPR is putting a time limit on the need to get this right.
“The amount of data captured by businesses every day can be a huge asset, unlocking valuable insights and creating competitive advantage. However, this same information can also cause serious headaches for those tasked with securely storing and managing it – and GDPR is putting a time limit on the need to get this right.